If your employees work from home then you know how much more efficient and productive having a remote workforce can be. Working from home is a great benefit to both user and employer, but an unsecured home network poses a threat to both corporate resources and the integrity of the company if it cannot be secured. By nature home networks aren’t very secure because the need to secure home networks with the same ferocity as workplaces with highly sensitive data has not been there. Also, home networks have been more affordable because their security requirements have been less rigorous.
While remote working has been around for some time, the pandemic elevated the home office from a novelty to a mandatory need in 2020. This shift in paradigm was met with praise and challenges at the same time; challenges that a Zero Trust Architecture (ZTA) can help address. ZTA’s concept principles of never trust, providing the least access needed and assuming there is a breach provides a much-needed level of security. Government and businesses are already moving in this direction. Using a form of ZTA principles can help make a remote workforce safer by providing a higher level of security.
The New Model and Market for Cybersecurity
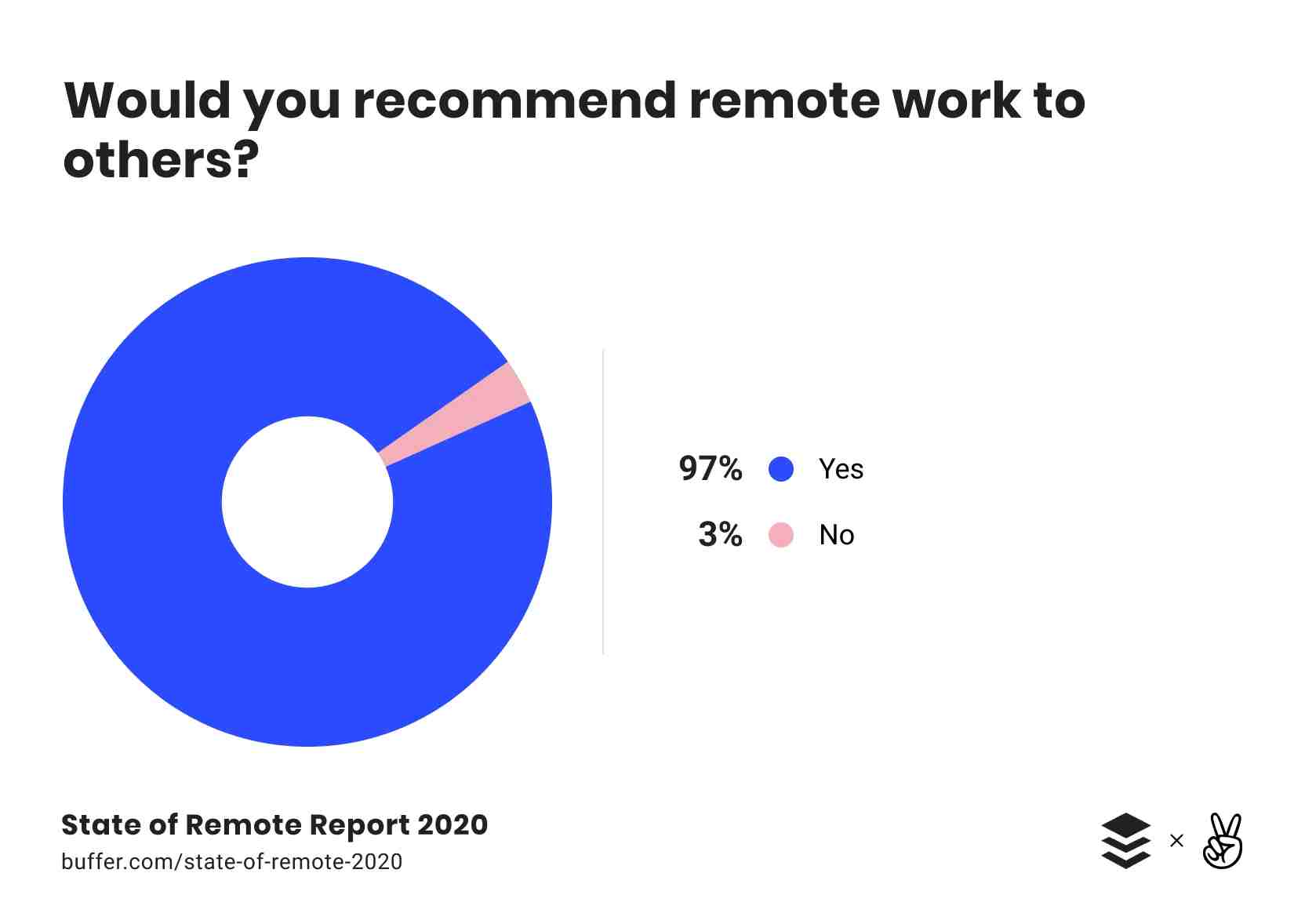
More people want to work from home and more people recommend it. Working from home has opened up a new level of freedom, creativity and best part, for companies, productivity. From: State of Remote Work (Figure 3C)

The trend for employees to work remotely, even part time, has shown that there is a tremendous new opportunity for cybersecurity companies to capture this emerging market. The growth of the remote office and cybersecurity concerns have created the new market for home/office security. Many home office solutions don’t have a sufficient network security setup that meets the requirements that businesses need to keep data safe.
With users accessing office resources from potentially unsafe home office networks, co-working spaces, and even local coffee shops, there has never been a greater demand for cybersecurity solutions for the remote workforce. The solution that has come of age to secure a business’s network and data is the Zero Trust Network Architecture (ZTNA) which will protect both the company and the home office.
Zero Trust Solutions to Move Forward
To reach a ZTNA solution at the home office or remote user level is the challenge. It is important to note that a ZTNA solution isn’t based on one product or system alone. The combination of software and hardware solutions together provide the ZTNA protection solution needed. MindPoint Group has a keen sense of what zero trust solutions can work in a remote environment that are effective and cost friendly.
Here are some recommended changes that can be done today:
- Complex Password – The computer password needs to be 12 characters or more with an alphanumeric password. Do not use easy to crack password such as “Password1234” as this is considered poor or low security. A good Password example is “P@p@D0ntPr3@cH!”.
- Screen lock – Turning on this feature provides automated protection if the computer is left unattended. A screen lock needs to activate after 5 minutes of inactivity.
- Behavioral Biometrics – This type of behavioral software recognizes when someone else uses your system. If someone else starts typing on your system the program will send the system into a screen lock state. (Example of Recommended Software: Typing DNA)
- Malware/ Virus Protection – Software that is designed to stop virus and malware from infiltrating the system from sources such as web pages, emails, compromised USB devices and software installs. (Example of Recommended Software: McAfee, MS-Defender, Norton, AVG or Avast )
- Encrypted VPN – A VPN is a virtual private network that allows you to access resource beyond the local network in your current residence, MiFi or hotel space. VPNs are used to connect remote users back to corporate resources. (Example of Software/Hardware: Open VPN, Ubiquiti, Google’s BeyondCorp or advanced firewall configuration)
- User Authentication (ICAM) – Managing personal identification information for accessing resources is critical. Secure your data by installing tools to ensure who can access the information. (Software: UI Verify, OneLogin, Auth0, miniorange or loginradius)
- Cloud Security – Store important documents in network cloud resources that have security features in mind such as AWS by Amazon, Azure by Microsoft or accessing Google’s cloud using their combined security model BeyondCorp.
- Network Security – This solution involves a basic network router/firewall that has more robust features such as IDS/IPS, Geo blocking, Syslog, Radius and WiFi Monitoring. It is important to separate the internal LAN from any guest device by network segmentation. (Hardware examples: Fortinet, Cisco and Ubiquiti) Note: May involve a higher cost to secure.
A business depends on a reliable network that has speed, efficiency and security to protect critical business information. How safe is the information of your business as it is being accessed remotely and what do you need to do to secure corporate resources? The principles of Zero Trust seeks to provide the resource to answer these questions. Many companies today have faced breaches in the security of their network because of inadequate security parameters. Providing better security on remote corporate resources and access into the network are the next steps to keeping your business running reliably and out of the hands of cyber thieves. MindPoint Group has years of experience in the Cyber Security sector. For years MindPoint Group has guided government institutions through the unforeseen dangers in a digital world. MindPoint Group now delivers the same tried and true reliable approach for business continuity and security to the home office. This article merely touches on some of the ways ZTA can help secure your workforce. By working with a leader in Cyber Security like MindPoint Group, we can help secure your growing workforce environment from wherever you choose to do business.
Author: Bruce Taylor







