Critical HPE 3PAR Vulnerability Discovery Details
This blog covers a recent security vulnerability found by a team of Pen Testers at MindPoint Group during a customer engagement. We'll walk through the issue descriptions, steps to reproduce the vulnerability, and our recommendations for remediating.
Common Vulnerability Exploit (CVE):
CVE-2019-5396
CVE-2019-5398
Severity:
Risk: Critical
Difficulty to Exploit: Easy
Vendor:
Hewlett Packard Enterprise (HPE)
Versions Affected:
HPE 3PAR Service Processor prior to 5.0.5.1
Discovered by:
Elwood Buck, Nolan Kennedy, and Dorian Aylward
Summary:
Authentication bypass and stored XSS vulnerability in HPE 3PAR Service Processor prior to 5.0.5.1 allows remote unauthenticated attackers to extract sensitive information and embed malicious content into the appliance.
Issue Description:
Stored Cross Site Scripting (XSS) attacks occur when data is included in dynamic content that is sent to a web user without being validated for malicious content. The content takes the form of JavaScript that the browser may execute. Common attacks based on XSS include:
- Transmitting private data (cookie & session information),
- Redirecting the victim to attacker-controlled web content, and
- Performing malicious operations on the user’s machine.
Steps to Reproduce:
Since this finding was identified in the last hour of the last day of an engagement it is not the most thorough PoC. However, it should still provide an overview of the substantive issues while also reminding us to never give up on time-constrained penetration tests. It can be helpful to walk into engagements thinking that there is a vulnerability, and we just have to turn over the right stone to find it. This reminder may be particularly helpful when you’re testing the same application 2-3 times over the course of a year or two, and you think that there is nothing left to find.
After manually reviewing the application GUI as an unauthenticated user, we switched on burp and noticed the application was displaying sensitive information when making calls to the preferences service endpoint. Specifically, we noticed that the responses included HREFs to what appeared to be valid user email addresses and the corresponding user preferences. We ran the HREF URLs through burp and received passwords to an SMTP server and other sensitive information: names, locations, addresses, etc.
We collected the displayed information and decided it would be worthwhile to attempt to change the values. We replicated the syntax provided to us when querying the preferences URLs for the banner message value (sensitive information sanitized):
{“defaultvariable”:true,”isMenuItemChanged”:false,”isdefault”:false,”name”:”globalprefs-login-banner-msg”,”uri”:”https://targetip:port/foundation/REST/preferencesservice/emailaddress@email.com/preferences/86713”,”value”:”<script>alert(123)</script>”}

We switched the request from GET to POST, added the Content-Length, Content-Type, and our JSON payload and fired it off. We re-navigated to the login page where the banner message was displayed, and it worked!
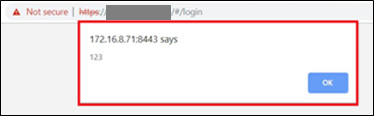
In addition to collecting sensitive information that could be used for further exploitation, we were planning on using the stored XSS to capture usernames and passwords after legitimate users logged into the appliance. Stored XSS is always bad, but being vulnerable on your login page can be especially detrimental.
Thanks to HPE for the quick turnaround and responsiveness to addressing the vulnerabilities we reported to them. They also gave us recognition on their security advisory!

Recommendation:
We were unable to get to the root of the authentication issue but it appeared that the API portion of the application did not perform user validation through session tokens, credentials, or an API key.
Follow OWASP's guidance on authentication and XSS mitigation.
References:
https://support.hpe.com/hpesc/public/docDisplay?docLocale=en_US&docId=emr_na-hpesbst03942en_us
https://www.owasp.org/index.php/Top_10-2017_A5-Broken_Access_Control
https://owasp.org/www-community/attacks/xss/
Timeline:
6/4/2019 – Vendor notified and ticket assigned
7/9/2019 – Patch released
8/1/2019 – Security advisory published
MindPoint Group's Pen Testing Services:
The vulnerability listed above was an unknown vulnerability, found during one of our pen testing engagements. MindPoint Group offers a variety of Security Operations services (like pen testing) to help your organization identify and mitigate risk and defend against ever-growing threats. Contact us to learn more.






